Cyber threat analysis [updated 2021]
What is a cyberthreat?
A threat could be anything that leads to interruption, disruption or destruction of any valuable service or asset within an organization’s technology ecosystem. Whether of “human” or “nonhuman” origin, a cyberthreat analysis must scrutinize each potential vector that may bring about conceivable security risk to a system or asset.
To support an organization’s efforts to identify, remediate and prepare for potential threats, cyberthreat analysis provides a structured, repeatable process. The outputs of the process are combined with the knowledge of internal data and external guidance and recommendations concerning the vulnerabilities pertinent to a particular organization. Finally, the vulnerabilities identified are evaluated to define their probability of occurring and their potential impact.
In other words, this threat-oriented approach to defending against cyberattacks represents a transition from a state of reactive security to a proactive one. Ultimately, an organization identifies how it can better protect the availability, confidentiality and integrity of its technology assets without affecting their usability and functionality.
Components of threat analysis
There are several different methodologies that organizations can use to perform cyberthreat analysis, but each, at a core level, shares the following key components or phases:
Fig.1
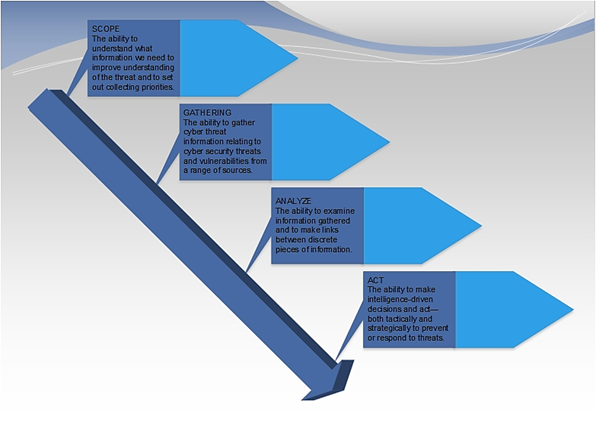
A. Scope
The scope includes the information, features of the asset or software and the threat environment that will be included in the analysis.
B. Data Collection
An IT analyst must have unrestricted access to data to transform it into intelligence that will inform their threat analysis. Sources of information are, for example, intrusion incidents, detection system logs, reported exploitations, firewall logs, the reverse engineering of malware, open-source internet searches, honeypots, digital forensic analysis and more. Other sources include internal policies and procedures, logs and alerts and system version and configuration information.'
C. Threat analysis
In this phase, systems, assets and enterprise security tools are tested and evaluated against the information gathered to determine where potential threats could be. For each threat identified, the organization will also determine the probability that the threat will be realized as well as the potential impact(s) if the threat is exploited. These potential impacts can be categorized by those that impact the availability, confidentiality and integrity of the system or data it processes or stores.
As part of this process, the threat analyst should also identify the attack vectors or the means to which a threat can be introduced to a device, system or network. Example attack vectors can include:
- Phishing attacks
- Unsecured wireless networks
- Removable media
- Mobile devices
- Malicious web components
- Viruses and malware
It is also important to note that the threat analysis should occur regularly. This could be at least on an annual basis or when there are changes or additions to the technology or operational footprint of the organization.
D. Mitigation and acceptance
Once all threats have been identified, the organization must then determine which vulnerabilities will be mitigated and which will be accepted. This acceptance can be due to the cost or difficulty of the remediation, its low probability of occurrence or even its potential to disrupt business services if altered.
Whatever the decision, each action and decision should have the approval of the organization’s executives, confirming that they agree with the resolution.
Approaches to cyberthreat analysis
How an organization chooses to work through the threat analysis process can vary, but ultimately, the process should be repeatable, based on industry best practices and structured to ensure that the full scope of the organization and its potential threats are evaluated.
The following are several of the potential methodologies that can be used to perform threat analysis.
Threat metrics
The process of threat measurement can help an organization capture and identify trends in system behavior and help to identify when anomalies occur. It can also underscore the prominence of certain types of vulnerabilities or be used to link unusual behavior to potential consequences. Unfortunately, defining and applying threat measures, or scores that reflect their probability and impact can be an art as much as it is a science.
While the probability of occurrence can vary and the impact may be hard to fully quantify, the exercise of identifying, measuring and reporting on threats in a structured way has a lot of advantages. These include the ability to make data-driven decisions about security controls or investments, or justification for system changes.
Threat models
However, metrics alone are insufficient to capture an organization’s threat level. A combination of metrics with a structured approach to identifying and mitigating threats can allow for a more robust security posture. The process also helps to quantify different elements of threats and their impacts to reduce the subjectivity of the authors, which could affect the outcomes.
The following is a sample threat model and its associated steps.
Threat modeling process
Sample № 2

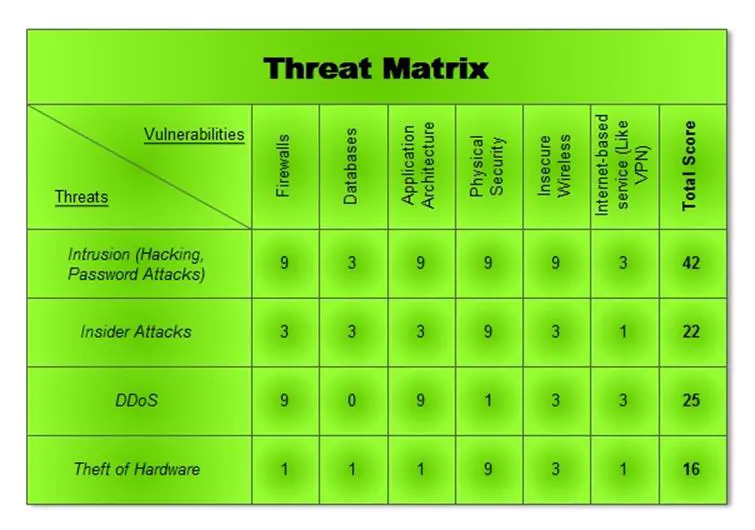
The threat matrix
In addition to threat models and metrics, a threat matrix uses attributes of a threat to help the analyst characterize the type of threat based on its overall nature. This kind of characterization allows analysts to describe the threat’s full spectrum while reducing the amount of subjectivity woven into their analysis. In other words, a threat matrix introduces levels, organized by characteristics or levels of magnitude, to consistently measure or describe each threat.
Threat attributes
It is a feature of a threat. Normally, there are two major groups of attributes, which analysts can use to evaluate a threat and its potential impact.
Commitment attribute group
The attributes in this group reflect the motivation or intensity of the threat or threat actor utilizing it. Three attributes exist in this group:
- Intensity How far the threat is willing to go?
- Stealth Do we have any confirmed information about the threat?
- Time How much time the threat is willing to invest?
Resource attribute group
The attributes here indicate the characteristics or behavior of a threat. A higher value means that a threat is more sophisticated and may have a bigger range of use or result in a bigger negative income for its target. There are also three attributes in the resource family:
- Technical Sophistication What vulnerability is the threat targeting, how unique is its method, and how effective is it?
- Knowledge How much does the attacker know about the target organization or the vulnerability of the target system?
- Access How good is the threat actor’s ability to compromise or reach the target system?
Using the above questions as a guide, a threat analyst could generate a threat matrix such as the one below. This matrix compares the potential threat against each vector, or target system, and rates its potential impact.
The result can help an organization prioritize its resources in mitigating the systems against the most common attacks or those with the biggest potential impacts.
“Threat matrix” sample
Attack trees
An attack tree appears as a logical diagram and it can be used either as a part of a range of threat analysis tools or on its own.
Attack trees are a structured and hierarchical way to collect and document the potential attacks on a given organization. The tree breaks down the types of attacks threat agents utilize and ties to them their goal or objective so the related systems or vectors can be identified.
Figure 2
Creating attack trees
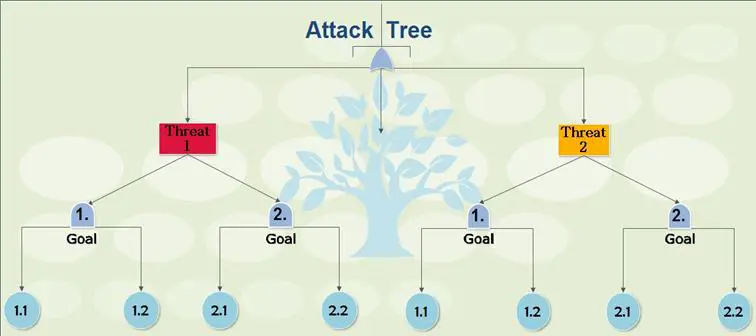

Benefits of attack trees:
- Threats can be broken down into their component goals and sub-parts so organizations can more fully understand the threat.
- The methodology is visual and easier for many different types of stakeholders to assist in developing.
- They are flexible in structure to cover the entire spectrum of attacks and threats.
- The data generated can be combined with other threat models.
Using what you know about threat analysis
In April 2014, the U.S. Department of Justice Antitrust Division and the Federal Trade Commission (FTC) released a joint statement on creating a uniform policy and mechanism for mutual threat information exchange. This policy and practice have the potential to enhance “the security, availability, integrity and efficiency of the nation’s information systems,” as organizations will have more data from which to understand potential threats and the impacts that they are having on their peers.
Steps like these demonstrate the public and private sector’s investment and determination to band together to proactively fight back against the growing cyberthreat. And while the techniques, tools and vulnerabilities used will continue to evolve, consistently performing cyber threat analysis and taking the needed steps to mitigate and remediate those issues found will only strengthen an organization's overall security posture.
Sources
- Risk Assessment and Threat Modeling, Apple Inc.
- Cyber Threat Analysis, not just for the Military, Cyber Squared Inc
- Information Security Risk Analysis – A Matrix-based Approach, Goel, S. & Chen, V
- Quantitative Metrics and Risk Assessment: The Three Tenets Model of Cybersecurity, Hughe, J. & Cybenko, G.
- CSOs need to more precisely understand the actual threats facing their organization. The fix? Threat modeling, Hulme, G.
- Cyber Threat Metrics, Mateski, M., Trevino, C., Veitch, C., Michalski, J., Harris, J., Maruoka, S., Frye, J. (2012)
- Threat Modeling Principles, Microsoft
- Cyber Intelligence Threat Analysis, MSM
- RSA 2014: HP exec says security threat analysis should guide strategy, Richards, K. (2014)
- An Overview of Threat and Risk Assessment, SANS Institute (2002)
- Developing Your Cyber Intelligence Analyst Skills, Tripwire Guest Authors (2014)
Diagrams:
- Fig. 2 is based on information provided in Threat Modeling Principles by Microsoft
- (Representation of an attack tree paragraph).
- Retrieved on 07/08/2014 from http://msdn.microsoft.com/en-us/library/ff648644.aspx
- “Threat Matrix” Sample is based on Table 5: Threat Matrix for GE Energy, Wind Division that can be found on page 7 in Information Security Risk Analysis – A Matrix-based Approach by Goel, S. & Chen, V. Retrieved on 07/08/2014 from http://www.albany.edu/~GOEL/publications/goelchen2005.pdf






